Last year, I thought I’d had my worse day in business when I had to repackage inventory costing $2000. That seems like a walk in the park now. Without doubt, the worse moment of my 10+ years online was getting hacked.

When you get hacked it feels like you’ve got a nasty infection and no one wants to get near you. Peoples’ faces screw up when you mention it. Previously helpful online collaborators suddenly give you the cold shoulder. Having an intruder in your hosting account looks bad. You’re unprofessional, unsafe, and dangerous to know. People don’t want to associate with that.
It’s like the stigma associated with catching an STI. Because no one wants to talk about it, you can’t find out what to do when you get hacked. This lack of information sharing exacerbates the problem.
Dealing with a hack
I would rather be robbed. Dealing with a hack means finding the vulnerability that lead to the intrusion, plugging it, finding out what other malicious materials were left by the intruders on all sites on that server, painstakingly cleaning up the mess (which has been cleverly hidden away) and moving hosts or servers. It costs so much time.
Dealing with a hack is like getting divorced: You’ve got endless amounts of shit to deal with and it’s all your fault. Security professionals are just like divorce attorneys. They’ll screw you at impressively high hourly rates whilst blaming you for everything that happens before, during and after.
It’s. All. My. Fault. I know. Thanks for reminding me.
So, how did it happen? And the blame game
It’s estimated that only 44% of web traffic is from human beings. The rest is from bots, hacking tools, scrapers, scammers and spammers. An estimated 37,000 websites are hacked every day.
There’s a saying in web security circles, “there are two types of website owners: ones who know they’ve been hacked and ones who don’t yet know they’ve been hacked.”The best hacks are undetected. Just imagine, Facebook, Amazon, and Google are probably getting hacked right now. And maybe they’re losing millions and they don’t know how or how much. Maybe that’s why they don’t pay tax. 😉
How did I get hacked? Unfortunately, I don’t know exactly. But a WordPress plugin with known vulnerabilities is the most likely candidate.
A website has a lot of moving parts: there’s the host, the DNS, the CMS, the plugins, the server configuration, the content, the functionality, etc., all have to be working correctly. Behind all these moving parts are human beings creating and running them. Humans make mistakes.
I want to be honest and transparent about what happened. Some humans maybe made mistakes which I’ll document, but I really want to emphasise how this was all my fault. I will also tell you what I’ve learned and if this helps anyone secure their site then it’ll be worth writing this article.

Being hacked is no fun. It turned me to drink. OK, that’s not true. But I don’t want anyone to be hacked. Not even the hacker. No more blame.
The story starts with membership plugins
Unfortunately, when I started selling video courses, platforms like Teachable were in their infancy. So, I decided to use WordPress membership plugins to protect and sell video content. Big mistake.
In December 2016, I was on my third WordPress membership plugin, called DAP (Digital Access Pass). (The fact that I’d been through three WordPress membership plugins tells its own story.) The Google Alert I have for “Rob Cubbon” alerted me to a mention of my name that I wasn’t so pleased about.
A site called OpenBugBounty.org reported that a “researcher” called “Spam404” had identified an XSS vulnerability affecting the learn.robcubbon.com website. I found “Spam404” via a quick google and I dropped him an email. He replied:
Glad you reached out. I would be delighted to share the details of this vulnerability with you. I found what’s known as a cross-site scripting vulnerability on learn.robcubbon.com. A malicious attacker can use this to execute JavaScript on your users.
The vulnerability was in the URLs of the buy buttons generated by DAP the membership plugin I was using. I immediately contacted DAP. They were aware of this vulnerability and were working on a new shopping cart that would cost $400. I paid the $400 and anxiously awaited the shopping cart update.
While I was waiting for the update, weird things started to happen
I first realised that something was wrong when people were telling me through social media that some of my course pages were redirecting. I tried to recreate the issue but couldn’t. However, after trying a few times, I saw this:
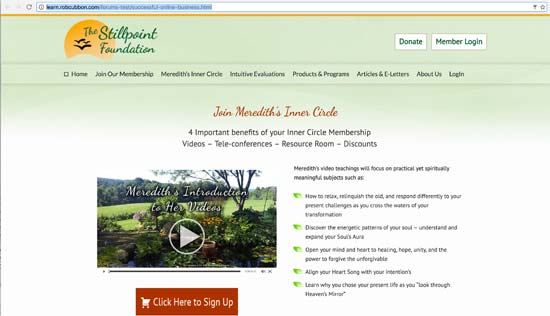
My heart sunk. Imagine clicking on an internal link on your site and seeing the sales page of a product you know nothing about. The above sales page is for a digital/membership access to a “life healing” product. The page was served from my site.
Looking at the site’s files on FTP, I saw where the above rogue HTML page was being served from. I immediately deleted that directory and everything I knew wasn’t “mine”. This was another of my mistakes. If you ever find files or directories on your server that shouldn’t be there, don’t delete them. Because, once the files are deleted you can’t find out who put them there (the IP) and when from the server logs. This could have provided essential information about plugging the vulnerability. I learned this from my host, Liquid Web.
I emailed The Stillpoint Foundation (see logo above) but I never heard back. It’s unlikely that they were responsible for the hack, of course. It’s more likely that they were hacked by the same hacker using the same technique and the hacker messed up. It’s pertinent that The Stillpoint Foundation site also uses DAP. This doesn’t confirm that DAP was the vulnerability that let the intruder in, but it makes it extremely likely. However, it could be that the hacker used the DAP vulnerability in a chain with other vulnerabilities to allow access to the site.
More details of the hack, and the hacker
A technician at Liquid Web did more routing around. He found that there was a publicly accessible file in /wp-includes/pomo/pomo.php that, when loaded in the browser, automatically logged you into WordPress’s backend as an administrator. This was the “backdoor into the WordPress backend”.
Using the logs, Liquid Web also tracked down another PHP injection that was likely used to create the pomo.php file: /wp-content/themes/twentyfourteen/inc/back-compat.php – another mistake of mine: I’d failed to delete unnecessary theme folders that were not out of date.
They deduced that the hacker was able to upload a malicious file that was then used to create and/or upload other files, one being a Shell script that granted access to the cPanel account as a whole, which in turn led to other compromises.
The attacker had high level access to the site and was able to duplicate sales pages in HTML with buy buttons going to his PayPal account. The sales pages would redirect to the duplicates sometimes but not always. This is to siphon off a percentage of sales but not everything. If a hack takes 100% of a site’s money, you’d notice straightaway – the best hacks lie undetected. I paid for one of my own courses through one of the hacker’s duplicate sales pages in order to identify the PayPal account.
Email used by hacker: brokerage.firm@hotmail.com
Name associated with PayPal email: haichun, sheng
I notified PayPal of the hack and they froze that account and canceled that payment and three others from my site. I’m actually quite surprised and a little incredulous that the hacker would have made any money. I have very few organic sales. All the sales come during email promotions.
By this point I was hard at work to make sure that this will never happen again.
What I did about the hack
Quite a lot…
Goodbye WordPress membership plugins, hello Teachable
As soon as it became obvious that my membership site at learn.robcubbon.com was a security liability, I did what I really wish I’d done years ago: sell courses with Teachable.
Teachable is a course selling platform you can redirect your domain to. It looks like you’re selling the courses but, in fact, the video storage and delivery, course protection, courseware, payment gateways, integration with email marketing platform, etc., is all being handled off your site and on the Teachable platform.
I love this. If a course video doesn’t play properly, it’s their problem. If a customer is having trouble accessing a course, it’s their problem. If the platform gets hacked, it’s their problem. After three years of having all the above as my problems, this is welcome.
There are many other benefits: setting up affiliates, bundling courses, and creating free or reduced price coupons is a breeze on Teachable. It’s as easy to sell courses on Teachable as it is on Udemy, but it’s on your site and you get the email addresses. It’s the selling platform of choice for over 50% of these 10 course selling experts.
The hacked learn.robcubbon.com site is no more and now redirects to my Teachable site at courses.robcubbon.com. I informed everyone who’d purchased a course previously with a free coupon to the free course on the new site.
Important: if you’re reading this and you think you purchased or enrolled on any courses at learn.robcubbon.com and haven’t received an email notifying you about the shift to courses.robcubbon.com, then please contact me.
Checked all sites for further vulnerabilities and compromises
I sent 4GB of all my sites on that server to a penetration testing company to be “cleaned” of all malware.
Although I’m 99% sure that the attacker came in through the DAP vulnerability and that vulnerability would have been “plugged” by nuking the site, I wanted to make sure the attacker didn’t place a “back door” anywhere to allow further access.
The penetration testing company didn’t find one, nor did they uncover any further evidence of the hack on learn.robcubbon.com, but they did find, rather shockingly, many further vulnerabilities and evidence of past hacks. Again, most of these were all my fault:
Various back-ups and other files with old versions of WordPress were found on site roots. Back-ups should be stored elsewhere on the server. Otherwise they can be extremely helpful for an attacker and further opens the doors for phishing and social engineering attacks.
Other files that were found lying around that could be useful to potential attackers were: php.ini.bak, error logs, htaccess.bak, phpinfo.php – if you have directory listing enabled these files can be read and provide valuable information to a hacker.
The most shocking revelation came from another of my sites, buildmybrand.net, that was a suite of tools that resized and edited images for social media sites. Multiple PHP backdoors (shells) were found in the web directory allowing attackers to execute arbitrary commands on the server. Some of the shells indicated automated attacks by multiple attackers.
I had employed a freelance developer to create the image manipulation tool with the aid of the Avery Image Editor add-on for Gravity Forms. He’d told me not to update the plugin or the site would break. Yeah, I know, another of my really stupid mistakes. Buildmybrand.net was used by a lot of people for free but had never made me any money, so I have nuked this site as well.
The penetration testing company showed me how lax I’d been with my web properties. There had been so many intrusions in the past it was frightening.

I’d even found evidence of intrusions myself after the clean up, included the above HTML calling card from Zero-X. Thanks, guys!
Set the cleaned sites up on a new server
After you have successfully plugged a vulnerability and removed all malware, it’s recommended that you change servers or hosts.
I’d planned on leaving Liquid Web as I’d been unhappy with some of their support with the hack. So I’d tried joining WP Engine. Unfortunately, I found manually setting up sites there too difficult and time consuming. I also had bad experience with their support.
So, I thought, better the devil you know, and I stuck with Liquid Web. I’m pleased now as I have since learned more about website security and now realise that web hosts aren’t wholly responsible for website security.
As I’ve said before, this hack was all my fault. It’s just nice to find someone to blame sometimes.
Hardening WordPress and my server
There is so much to say here that I’m going to do another blog post on WordPress security. In the meantime here’s a video on some WordPress security hardening tasks that each take a minute that you could action right now.
And here’s a synopsis of what’s coming in my post:
- Regularly change hard to remember passwords
- Make regular back-ups stored off-site
- Update WordPress core, themes and plugins
- Delete unnecessary files and folders
- See if any files or folders have the permissions set to 777
- Disable directory browsing
- Only have your site’s administration areas only accessible by certain whitelisted IPs
- Password protect the /wp-admin/ directory
- Block scripts in /wp-includes/
- Prevent PHP execution in /uploads/ directory
- Deny access to anyone surfing for wp-config.php
- Disable file editing within the WordPress dashboard.
It’s also sensible to invest time into “webroot hygiene” and clean up your server of unnecessary files and folders. At the very least these are great places for attackers to hide malware. Look where my attacker placed one of the malicious files, in the unused Twenty Fourteen theme folder.
What have a learned from this unsavory episode
Apart from implementing basic security best practices, I’ve also concluded that WordPress is probably best used as a blogging platform. The most vulnerable websites are the ones that allow the most interaction with the user. I was trying to do too much with WordPress. For example, membership site plugins create multiple WordPress users which has security implications. And my online image editing tool allowed users to upload files. In a way, I was asking for trouble.
I also was pleased that I managed to stay quite cheerful during this unfortunate episode. When you work on your own business, it’s easy to feel isolated and stressed when things go wrong.
There were several things working in my favor:
- My business generates income from multiple sources and online platforms, selling courses from my own site is only one small part of the overall income.
- I was mostly living in Thailand (the Land of Smiles) for most of the time I was dealing with the hack.
- Whenever things got me down, I’d answer an email from someone who needed help. When other people are trying to put you down, it’s great to try to improve someone else’s life. Helping people makes you happy.
- After my worse day in business when I had to repackage inventory costing $2000 last year, I’m like: “Bring it on! Throw what you can at me!” I was more invested in my success last year and I’ve since tried to enjoy the moment rather than focussing on future events.
Time I shut up
Glad you made it to the end, my friend. I hope this article helped you in some way. And, remember, keep your WordPress plugins updated.

Even though Sucuri and automatic updates can make preventing hacks harder, its surprising at the neglect some clients have…. we had a prospect come to us who’s website had been hacked 5 months previously and they had only just realised 5 months later!
Some of the passwords we have seen as well “admin, admin” …. some people take security very light heartedly!
Hello Craig, well, shockingly I was guilty of some of this laxness with security so I can’t comment on your clients. But when you consider that good username and passwords procedure, updating software, a security plugin and regular back-ups will solve 90% of problems, it is amazing how many people don’t do the basics.
Thank you sooo much 🙂
Thank you, Olivier
Thanks for sharing this, Rob.
I use some .htaccess rules to protect my wp-admin. I also use plugins like Sucuri etc.
What do you think about Restrict Content Pro and Paid Memberships Pro as membership solutions ?
Hello Alexander, I don’t know about Restrict Content Pro and Paid Memberships Pro so I can’t comment. But I’d never use a WordPress plugin to sell video courses, Teachable has been so much better, and safer, in this regard. I hope this helps. Let me know if you have any questions.
Thanks for such an upfront post, Rob. I’ve been in the hacked club too, and it’s not fun.
I guess the worst part for you was finding out that it had gone on for such a long time. 🙁 I see that the DAP vulnerability was highlighted in 2014. It might be a good idea to subscribe to some security blogs.
At least you’re aware of the dangers now and can warn others.
Looking forward to reading your post about the security measures you’re taking.
Hello Claire, that was actually a different DAP vulnerability to the one I think was used to gain access to my site. DAP has a history with vulnerabilities and can’t be used on WP Engine, etc., I think there were enough red flags!
I think Wordfence is an excellent mailing list to subscribe to – they’re coming out with loads of interesting stuff at the moment.
Sorry to hear we’re both members of that infamous hacked club. At least we’re wiser now!
Wow – thanks for this post. I’m guessing it was an emotionally difficult one to write, too. The whole experience made me twitchy just reading it. (Been hacked, but just took down the whole site.) However, kudos to you for handling it so well and seeing it all through to the cleanup. And after all was said and done, you generously gifted us your experience as a teaching moment. As Shakespeare said, “Shit happens; it’s how you deal with it that makes the difference.” –Melvin Shakespeare
Hey, Annie, loving that Melvin Shakespeare quote. Thank you so much for your kind words. I guess it was emotionally difficult in a kind of 1st world problem way. 🙂 Sorry to hear you’ve joined us in the “We’ve been hacked” club!
Hi Rob,
Thanks for the article, I been following you for a long time and you are always providing great ideas.
Is so sad that we live in a time that we after be watching over our shoulders. But I do appreciate that you took the time to provide this experience. So Rob sorry for what happened to you but all the best!!!
Thank you, Antonio, for your kind words and for following me for long. Yes, it’s sad, but if you follow the basic security procedures, you should be safe from this. 🙂
Many thanks for the headsup Rob!
Very timely for me.
I guess we’ll allways be open to attack, to some degree.
But being aware takes away some of the sting.
Keep up the good work.
Hello Andy, Yahoo’s been hacked, Amazon’s been hacked. The US Government was hacked. So I guess we’ll allways be open to attack with a mere WordPress website!
Definitely it pays to be aware and to employ the basic security processes.
Hey Rob,
First of all – sorry to hear about this situation.
But I love how you take “extreme ownership” of it all. 🙂
If I may, I’d love to share a few (hopefully useful) items with you and your audience in addition to the goodness you’ve already shared.
I have – for better or for worse – copious experience in this area.
1. Unfortunately I’ve seen and cleaned up this exact hack on several DAP sites now.
It seems that the hackers target DAP sites because it’s easy to replace the DAP buy button with a Paypal button leading to their accounts.
Then they often go in and manually add the buyers so as not to arouse suspicion.
The cruder hackers simply redirect the sales pages to HTML versions with their bogus buy links.
To be clear, in most of these cases the actual back door wasn’t from DAP itself but from another plugin like OptimizePress, BlogVault, Xenforo (an external non-WP forum script), etc.
It’s DAP they were targeting but not DAP they were exploiting.
2. In terms of a security plugin I’d highly recommend WordFence.
Even the free version is amazing, the only thing really lacking is 2-factor authentication.
Which, if you’re serious about security, 2FA will really cut down issues but may also be a pain in the butt.
Also, the WordFence team is really on top of their game.
They send out “day 0” emails on recently discovered hacks, post useful info on their blog, profile criminal organizations that exploit websites, and basically serve as a great educational resource for all things WP security.
3. You wrote:
“Security professionals are just like divorce attorneys. They’ll screw you at impressively high hourly rates whilst blaming you for everything that happens before, during and after.”
In my estimation those are the hallmarks of a non-professional.
However, it points to a larger and more fundamental problem about hosting.
The vast majority of hosting companies, whether they’re shared, VPS, “Managed WordPress”, or whatever else – almost all of these hosting providers expect YOU (the end user) to manage the admittedly rather technical aspects of server and application security and performance (speed).
That’s a tall order for the vast majority of site owners, even those who are technically inclined.
It’s not, and shouldn’t be, their concern.
Yes it is.
That’s a disconnect that I’m working very hard with my team at SpeedKills.io to address because in the WordPress hosting space you get your server and then “see ya” – security, speed, and all the rest of it is now YOUR problem, which isn’t cool (unless you have a weird fetish for sending sys admins and developers lots of your hard earned money!)
You’re right, Rob, in that WordPress is inherently insecure by its very nature.
Whenever you can go with a 3rd party platform like Teachable (for courses) or TypeForm (for forms) or ClickFunnels (for Funnels), etc., it’s definitely the more secure option.
But if you’re stuck with a Frankenstein’s monster of WordPress plugins and themes because that’s the only way to accomplish the functionality that you need, then security becomes commensurately paramount.
4. Finally, perhaps you and your audience would find our internal WordPress security procedures to be of use.
Our security and malware removal expert, Cristian, wrote these and they reflect what we *actually* do in terms of prevention and remediation / hardening.
https://docs.google.com/spreadsheets/d/1ol-aGuJbzhwZJbjmqe8f4nbPmXd13nbVPLlawwZmEIs/edit?usp=sharing
Be safe! 😉
Vic, Founder – SpeedKills.io
Hey Vic,
1. It was likely that the DAP buy button vulnerability was the target, it’s also possible that it wasn’t the entry point as you say. However, I wouldn’t use a plugin that is being targeted. Considering that it’s fairly possible to hack just about any WordPress website, leaving a target in there is not something I’d ever do or advise from now on.
2. Yes, I totally agree with you about Wordfence. I have the free version on all my sites and the paid version on this one.
3. I was talking about the people at the penetration testing company who “cleaned” the sites as well as the OpenBugBounty researchers who alerted the world to the vulnerability. These people I found to be expensive and arrogant. Not the hosts. The hosts aren’t security experts. They’re hosting experts. I think that is an important point, that’s why I’m saying that, at the end of the day, your site’s security is your responsibility. A responsibility that I, sadly, didn’t take seriously enough.
Sure hosts can do more. We could all do more. I was pissed off a little at Liquid Web. I would have liked to move to WP Engine but it was a shame their pre-sales support was so poor. But I’m happy with my current set up with Liquid Web as I’m more aware of what they’ll do and what is my responsibility now.
4. Best of luck with your new venture with Christian it’s certainly is worthy and necessary that your putting heavy importance on security. Thanks for the Google doc. I’m doing a new WordPress security post that will mention all of these security procedures.
All the best, Vic!
Rob
WordPress is the most vulnerable platform due to its plugins. Most of the time site developed is hacked because wordpress.org do not think that it is necessary to review the code written by contributors who are not so experienced
Well, I’m not an expert but I would say, in WordPress’s defence that great success brings with it greater scrutiny. It grew from nothing to powering 20% of the world’s websites in a few years. One of the reasons of its initial success was the adaptability the plugin system gave it. And I think they do have some criteria to be on the repo. And I know security is a huge department in Automattic.
But for whatever the reasons, Sam, you are right, it’s a vulnerable platform now compared to the smaller ones, Squarespace for example. And it pains me to say that because I think WordPress was responsible for building a gazillion successful businesses, mine included, (and allowed me to stop working at a JOB!)
so bad news rob, but always i not recommended WordPress as marketing solution for my client,it is still not mature solution for dealing with money and fit to blogging.
i hope you will understand the lesson very well and if you need any advice from me i am ready my friend , more times i took advice from you and now the time to return the favor
Hello Ahmed, thank you for your comment. I understand you not recommending WordPress but I still would recommend WordPress to use as a blogging platform as long as you employ the basic security procedures. It’s not a case that one platform is secure and another one isn’t. Any site can be hacked. There’s a chance we’ll be here in five years time talking about WordPress’s successor being vulnerable. I think WordPress was a victim of its success.
Ok so I understand that you are using Teachable for selling your video courses but are you using any other non-wordpress membership platform for other purposes; OR what would you recommend for membership platform now if needed?
Not sure if I understand the question, Amy, I would recommend Teachable or Thinkific for selling courses, both are off WordPress’s platform and I think that’s best. I hope this helps. Let me know if you have any questions.
Sorry about that! Ok what I mean is: if you needed to use a membership plugin on your site like for reason’s other than selling courses what would you recommend now?
Like if you had pages for just certain members, that need separate logins – something that might possibly handle for instance from 20 up to 300 people maybe?
I’ve been struggling with this for a long time trying to find the best fit, and they all struggle with one part or another, very frustrating. Unfortunately on one site we experienced a hack also and boy have I developed a huge security plan that I use on all my sites now…. uggg I so feel your pain 😉
It’s so interesting that over the last year I keep telling myself that unless someone wants specifically a blog, I will go in a completely different direction; I developed that feeling just out of my very own pure experience and here I read about you and your experience with a hack and you are saying exactly the same thing…. I now spend more time monitoring security and being paranoid about it then I do working on actual sites. I also still love wordpress but that part is becoming way to time consuming which costs too much $$$$$$!!
Hi Amy, I would say that initially I would avoid membership sites on WordPress. They have to create new WordPress users for the members and, although I’ve got no proof that that is a vulnerability, it gives me the creeps. I just don’t like them. I would search for another solution. Instead of selling access to certain pages, sell PDFs on Gumroad – it’s easier, cheaper, and more safe.
That being said, if I had to, I would probably choose WishList Member. It’s been around for a long time, I haven’t heard about security vulnerabilities, and it’s one of the cheaper ones. Having said that I would search on Upwork or elsewhere for a WLM expert developer who can help you get it to do what you want.
I hope this helps. Let me know if you have any questions.
You may find this article helpful – the methods of 10 of the most successful online instructors use to sell courses: https://robcubbon.com/million-selling-online-courses-tips-experts/ – most of them use Teachable. Troy Dean uses LearnDash. I hope this helps. Let me know if you have any questions.
WOW Rob, THANK YOU, for all of that GREAT info!! Soooooo much appreciated!
I will check out all of these resources, I am familiar with WishList Member, but the others I will check out!
I started a new practice last year and that is: if I need new functionality for a WordPress site can I accomplish the same thing WITHOUT adding a new plugin and you know what? I’ve been able to accomplish that now almost every time by finding other ways! Less plugins is way more as far as safety!! I learn a lot more too …. 😉
Good luck to you !
Hey Amy, that’s great. Less plugins also means more speed. 🙂